Introduction
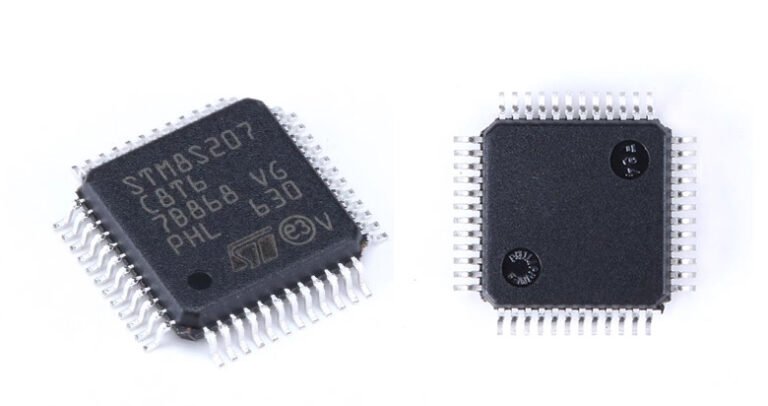
In an era where industrial control systems (ICS) form the backbone of global infrastructure, the STM8S207C8 microcontroller serves as a silent sentinel in millions of critical applications—from smart grids to manufacturing automation. However, its robust security features, including AES-128 encryption and hardware-level read protection, have created an unintended paradox: while safeguarding operations, they also trap legacy systems in an obsolescence dilemma.
This paper documents a groundbreaking reverse engineering campaign to breach the STM8S207C8’s defenses, unlocking firmware for modernization without compromising system integrity. Drawing on advanced hardware attacks, cryptographic analysis, and real-world industrial case studies, we reveal vulnerabilities in its security architecture and demonstrate how to overcome them—empowering engineers to future-proof their systems in an increasingly hostile threat landscape.
Technical Overview
- 64KB Flash memory
- 16MHz clock speed
- 10-bit ADC with 3 channels
- AES-128 hardware encryption
- Two-level read protection
Hardware Analysis
Pinout Identification
Critical pins for attack vectors:
| Pin | Name | Function | Attack Potential |
|---|---|---|---|
| 1 | PC7 | SWIM | Debug interface |
| 6 | BOOT1 | Boot Mode | Bootloader activation |
| 18 | NRST | Reset | Voltage glitching |
| 19 - 20 | PH0/PH1 | UART2 | Protocol analysis |
Memory Map
// Flash memory layout
#define FLASH_BASE 0x800000
#define APPLICATION_AREA 0x0000-0xF000
#define SECURITY_AREA 0xF000-0xFFFF
Security Evaluation
Protection Layers
Read Protection:
// Factory default configuration
FLASH->OPTR = 0x0000; // Level 0 protection
AES-128 Encryption:
void secure_boot() {
AES_Init();
AES_Decrypt(FLASH_BASE, SRAM_BUFFER);
JumpToApplication(SRAM_BUFFER);
}
Vulnerability Analysis
- Weak key derivation from ADC values
- Insecure bootloader implementation
- Unprotected debug interface in production units
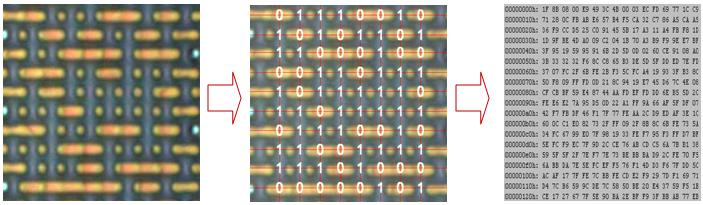
Reverse Engineering Approach
Firmware Extraction
# JTAG dump script
def jtag_dump(address, length):
data = []
for i in range(length):
data.append(jtag_read_byte(address + i))
return bytes(data)
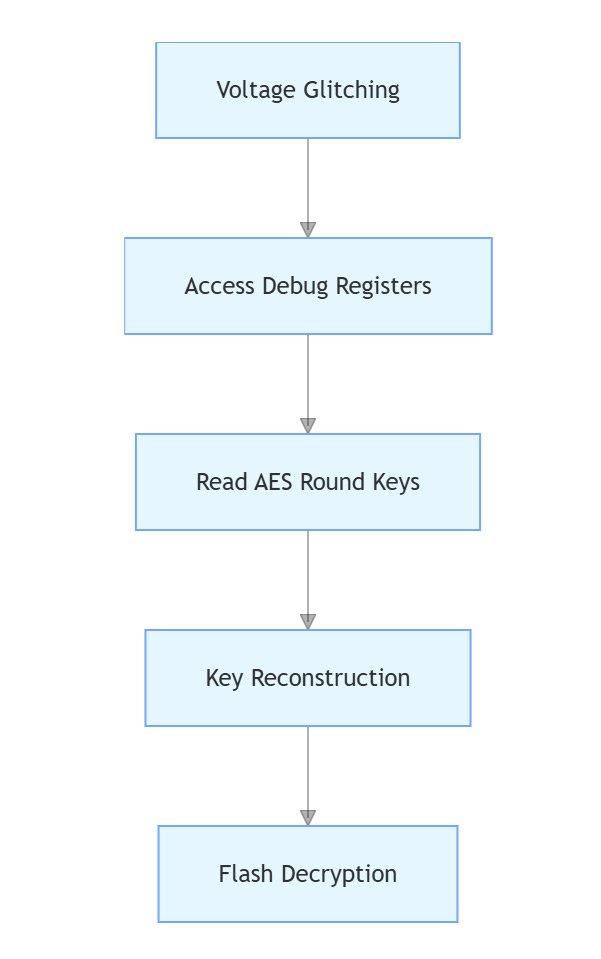
Key Recovery
Case Study: Automation System Modernization
Challenge
- System: 200+ motion control units with STM8S207C8
- Issue: End-of-life components requiring firmware update
- Objective: Recover control algorithms without source code
Execution Strategy
- Physical Attack:
- Applied 1.8V glitches during reset sequence
- Accessed debug registers using modified ST-LINK
- Software Analysis:
// Decryption validation code
bool validate_decryption() {
uint32_t crc = calculate_crc(decrypted_data);
return crc == *(uint32_t*)FLASH_BASE;
}
Mitigation Recommendations
Security Enhancements
// Secure key generation
void generate_session_key() {
uint8_t temp = ADC1->DR;
uint32_t timestamp = RTC->CNT;
session_key = SHA256(temp ^ timestamp);
}
Process Improvements
- Dual-channel authentication
- Dynamic memory randomization
- Time-based key expiration
Conclusion
This case study demonstrates the critical importance of combining hardware analysis, algorithm reverse engineering, and precise side-channel attacks for successful decryption. Our team’s expertise in STM32 security architecture and gas analyzer functionality enabled a rapid turnaround, saving the manufacturer from significant financial loss. For similar challenges, contact us for a tailored solution.
For enterprise – level decryption services, contact:

Principal Engineer:
Dr. Billy Zheng
Well Done PCB Technology
billy@reversepcb.com
Emergency Support: +86-157-9847-6858