IC Reverse Engineering

What is IC reverse engineering?
IC reverse engineering is also called integrated circuit reverse engineering, chip unlock, ic cracking, chip decryption. It is an process of reverse engineering upon the integrated circuit or microcontroller of encrypted products. In generally, this process allows programmers to read and copy the FLASH/EEPROM program of ICs to a new one.
Our IC reverse engineering Capability
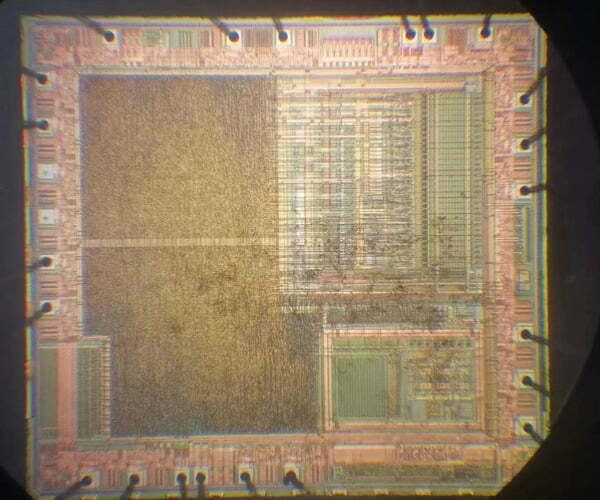
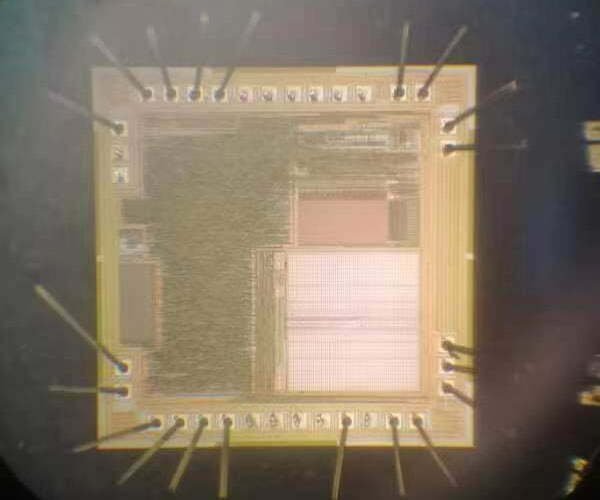
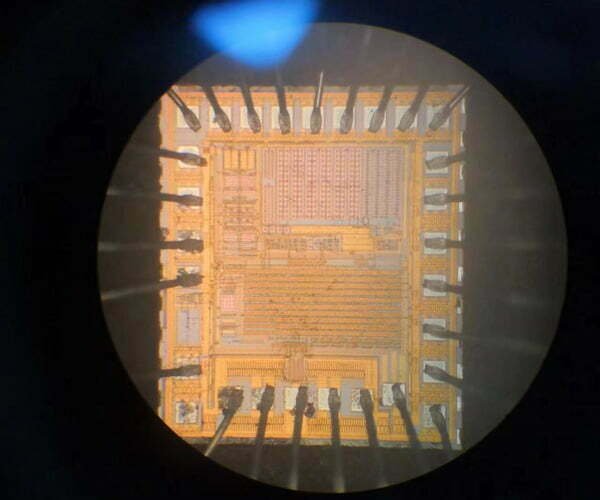
- International advanced IC testing algorithms and research;
- IC programming, disassemble bin files;
- FIB(focused ion beam), SEM(scanning electron microscope), TEM(transmission electron microscopy);
- Single-chip microcomputer (MCU) and DSP system development;
- Integrated circuit decrypting, designing and developing, failure analysing;
- Secondary development and upgrade of chip programs;
- Support IC types: DSP,CPLD,PLD,AVR,ARM;
- One-stop reverse engineering services for integrated circuit, semiconductor;
Supportable IC Series & Models
In past years, we have done over 1000+ IC unlock projects. Our customers range from start-ups to enterprises operating in various industries like manufacturing, IT & software, health care, e-commerce, telecom, real estate, e-learning, education, public sector and much more. We are also a preferred choice for businesses that wish to outsource their data entry and data processing tasks. For more IC models, please contact us directly.

STMicroelectronics
STM32F2 series:
STM32F205/215 STM32F207/217
STM32F4 Series:
STM32F401 STM32F405/415 STM32F407/417 STM32F410 STM32F411 STM32F412 STM32F413/423 STM32F427/437 STM32F429/439 STM32F446 STM32F469/479
STM32F7 Series:
STM32F7x0 STM32F7x2 STM32F7x3 STM32F7x5 STM32F7x6 STM32F7x7 STM32F7x9
STM32H5 Series:
STM32H503 STM32H562 STM32H563/573
STM32H7 Series:
STM32H723/733 STM32H725/735 STM32H730 STM32H742 STM32H743/753 STM32H745/755 STM32H747/757 STM32H750 STM32H7A3/7B3 STM32H7B0
STM32C0 & STM32F0 Series:
STM32C0x1 STM32F0x0 STM32F0x1 STM32F0x2 STM32F0x8
STM32F1 Series:
STM32F100 STM32F101 STM32F102 STM32F103 STM32F105/107
STM32F3 Series:
STM32F301 STM32F302 STM32F303 STM32F334 STM32F373 STM32F3x8
STM32G0 Series:
STM32G0x0 STM32G0x1
STM32G4 Series:
STM32G4x1 STM32G4x3 STM32G4x4
STM32L0 Series:
STM32L0x0 STM32L0x1 STM32L0x2 STM32L0x3
STM32L1 Series:
STM32L100 STM32L151/152 STM32L162
STM32L4 Series:
STM32L4x1 STM32L4x2 STM32L4x3 STM32L4x5 STM32L4x6 STM32L4P5/Q5 STM32L4R5/S5 STM32L4R7/S7 STM32L4R9/S9
STM32U5 Series:
STM32U535/545 STM32U575/585 STM32U595/5A5 STM32U599/5A9 STM32U5F7/5G7 STM32U5F9/5G9
STM32MP1 Series:
STM32MP131 STM32MP133 STM32MP135 STM32MP151 STM32MP153 STM32MP157
STM8 Series:
STM8AF52 STM8AF62 STM8AF63 STM8AL31 STM8AL3L STM8L STM8L101 STM8L151/152 STM8L162 STM8S103/105 STM8S207/208 STM8TL52/L53

Actel Microcontrollers Models
Actel ProASIC3 Series:
A3P1000 A3P250 A3P060 A3PE225 A3PE045 A3PE015 A3PE400 A3P015 A3P075 A3P050
Actel ProASIC3L Series:
A3P1500QC144-2 A3P1600QC144-2 A3P1700QC144-2 A3P1800QC144-2 A3P1900QC144-2 A3P2000QC144-2 A3P2200QC144-2 A3P2500QC144-2 A3P3000QC144-2
Actel ProASIC3E Series:
A3P500-FG144 A3P1000-FG144 A3P1500-FG144 A3P2000-FG144 A3P2500-FG144
Actel RT Series:
RT ProASIC3: RT ProASIC3E, RT ProASIC3L
RT ProASIC3 A3P: RT ProASIC3 A3P1000, RT ProASIC3 A3P250, RT ProASIC3 A3P600
Actel SmartFusion Series:
M2S010S-FG484 M2S010S-FG676 M2S015S-FG484 M2S015S-FG676 M2S030S-FG484 M2S030S-FG676 M2S050S-FG484 M2S050S-FG676 M2S100S-FG484 M2S100S-FG676
Actel RTAX-DSP Series:
RTAX2000S, RTAX4000S, RTAX8000S, RTAX-DSP-XL
Actel Axcelerator Series:
Axcelerator: AX1000, AX1500, AX2000, AX3000
Axcelerator LX: LX4, LX9, LX16, LX25, LX45
Axcelerator SX: SX8, SX12, SX18, SX35
Actel Analog ADUCxx Series:
ADuC70xx: ADuC7060, ADuC7061, ADuC7062, ADuC7064, ADuC7066
ADuC71xx: ADuC7121, ADuC7122, ADuC7123, ADuC7124
ADuC72xx: ADuC7222, ADuC7224, ADuC7226, ADuC7227, ADuC7228
ADuC83xx: ADuC831, ADuC832, ADuC834, ADuC836, ADuC838

Atmel Microcontroller Series
Atmel AT89xx Series:
AT89C51 AT89S52 AT89C1051 AT89C2051 AT89C4051 AT89LP51 AT89LP52 AT89C51CC02 AT89C51CC03 AT89C51RB2 AT89C51RC AT89C51RD2 AT89LP2051 AT89LP2052 AT89LP213 AT89LP214 AT89LP216 AT89LP4051 AT89LP4052 AT89LP828 AT89LP428 AT89LS51 AT89LS52 AT89LV51 AT89LS53 AT89LS8252 AT89LV52 AT89LV55 AT89S2051
Atmel AT90xx Series:
AT90S1200 AT90S2313 AT90S4433 AT90S8515 AT90S2333 AT90S4434 AT90S8535 AT90S4414
Atmel AT90CAN Series:
AT90CAN32 AT90CAN64 AT90CAN128
Atmel AT90PWM Series:
AT90PWM2 AT90PWM216 AT90PWM2B AT90PWM3 AT90PWM316 AT90PWM3B
Atmel AT91SAM Series:
AT91SAM7S AT91SAM7X AT91SAM7A AT91SAM7L AT91SAM7SE AT91SAM7S64 AT91SAM7S128 AT91SAM7S256 AT91SAM7S32 AT91SAM7S321 AT91SAM7S64B AT91SAM7XC AT91SAM7X128 AT91SAM7X256 AT91SAM7X512 AT91SAM9XE AT91SAM9N12
AT91SAM9M10 AT91SAM9RLEK AT91SAM9G45 AT91SAM9M11 AT91SAM9G20 AT91SAM9G10 AT91SAM9G45E AT91SAM9G15 AT91SAM9X35 AT91SAM9G25 AT91SAM9X25 AT91SAM9X55
Atmel ATTiny Series:
ATtiny13 ATtiny25 ATtiny45 ATtiny85 ATtiny2313 ATtiny24 ATtiny44 ATtiny84 ATtiny261 ATtiny461 ATtiny861 ATtiny4313 ATtiny48 ATtiny88 ATtiny167 ATtiny87 ATtiny1634 ATtiny828
Atmel ATMega Series:
ATmega8 ATmega16 ATmega32 ATmega64 ATmega128 ATmega162 ATmega169 ATmega165 ATmega323 ATmega325 ATmega3250 ATmega329 ATmega3290 ATmega640 ATmega1280 ATmega1281 ATmega2560 ATmega2561 ATmega16U2 ATmega8U2
Atmel ATF (Advanced Technology Flash) Series:
ATF15xx ATF16V8B ATF22V10C ATF22V10L ATF22V10Z ATF750LVC ATF750CLV ATF750CLL ATF750CV ATF750CLL

ALTERA Series
Altera EPM (Easy Power Manager) Series:
EPM3128A, EPM3256A, EPM7064S, EPM7032S, EPM7128S, EPM7256S, EPM7192S, EPM7128ELC84, EPM7256AETC100-10, EPM570T144I5N, EPM1270F256C3, EPM1270F256C3N, EPM1270F256C4, EPM1270F256C4N, EPM570GT144C5NLF, EPM570GT144I3N, EPM570GT144I5, EPM570GT144I5N, EPM570GTI144I5, EPM7256SRC208-7, EPM7256SRC208-7N, EPM7256SRC208-10, EPM7256SRC208-10N.
Altera Cyclone Series:
Cyclone V, Cyclone IV, Cyclone III, Cyclone II, Cyclone 10 LP, Cyclone IV GX, Cyclone IV E, Cyclone IV GZ, Cyclone IV GT, Cyclone IV GS.
Altera Arria Series:
Arria 10, Arria V, Arria V GZ, Arria V GT, Arria V SoC, Arria V ST, Arria II, Arria GX, Arria GZ.
Altera Stratix Series:
Stratix 10, Stratix V, Stratix IV, Stratix III, Stratix II, Stratix GX, Stratix GZ, Stratix DE2 Development Kit, Stratix V GX Development Kit, Stratix IV GX Development Kit, Stratix III Development Kit, Stratix II GX Development Kit, Stratix II Development Kit, Stratix GX Development Kit, Stratix GZ Development Kit, Stratix 10 GX Development Kit, Stratix 10 TX Development Kit.
Altera MAX Series CPLDs (Complex Programmable Logic Devices):
MAX II, MAX V, MAX 3000A, MAX 7000A, MAX 7000B, MAX II CPLD Board Design Kits, MAX V CPLD Board Design Kits, MAX II CPLD Evaluation Kit, MAX V CPLD Evaluation Kit.
Altera MAX 10 Series:
MAX 10 FPGA Series, MAX 10 NANO Series, MAX 10 FPGA Development Kit, MAX 10 NANO Development Kit, MAX 10 FPGA System-On-Module (SOM) Kit, MAX 10 NANO System-On-Module (SOM) Kit

MICROCHIP Microcontroller
PIC Microcontroller Series:
- PIC10F: PIC10F200 PIC10F202 PIC10F204 PIC10F206 PIC10F220 PIC10F222
- PIC12F: PIC12F1501 PIC12F1822 PIC12F1840 PIC12F509 PIC12F510 PIC12F675 PIC12F683 PIC12F752 PIC12F1571 PIC12F1572 PIC12F1612 PIC12F1613 PIC12F1840T39A PIC12F1840T48A
- PIC16F: PIC16F1454 PIC16F1455 PIC16F1458 PIC16F1459 PIC16F1503 PIC16F1507 PIC16F1508 PIC16F1509 PIC16F1512 PIC16F1513 PIC16F1516 PIC16F1517 PIC16F1518 PIC16F1519 PIC16F1526 PIC16F1527 PIC16F1574 PIC16F1575 PIC16F1704 PIC16F1705 PIC16F1707 PIC16F1708 PIC16F1709 PIC16F1713 PIC16F1716 PIC16F1717 PIC16F1718 PIC16F1719 PIC16F1782 PIC16F1783 PIC16F1784 PIC16F1786 PIC16F1787 PIC16F1788 PIC16F1789 PIC16F1823 PIC16F1824 PIC16F1825 PIC16F1826 PIC16F1827 PIC16F1828 PIC16F1829 PIC16F1847 PIC16F1933 PIC16F1934 PIC16F1936 PIC16F1937 PIC16F1938 PIC16F1939 PIC16F1946 PIC16F1947 PIC16F87 PIC16F88 PIC16F819 PIC16F820 PIC16F872 PIC16F873 PIC16F874 PIC16F876 PIC16F877
- PIC18F: PIC18F452 PIC18F4550 PIC18F46K22 PIC18F4620 PIC18F67K22 PIC18F87K22 PIC18F97J60 PIC18F26K40 PIC18F2620 PIC18F27J53 PIC18F8722 PIC18F66K80 PIC18F86K80 PIC18F66J11 PIC18F86J11 PIC18F63K22 PIC18F83K22 PIC18F26J50 PIC18F27J13 PIC18F46K80 PIC18F47K40 PIC18F67J60 PIC18F87J60 PIC18F66J60 PIC18F86J60
- PIC24F: PIC24FJ128GA010 PIC24FJ128GA306 PIC24FJ256GA705 PIC24FJ256GB106 PIC24FJ256GB108 PIC24FJ256GB210 PIC24FJ64GA002 PIC24FJ64GA004 PIC24FJ96GA006 PIC24FJ128GA008 PIC24FJ128GA010 PIC24FJ128GA306 PIC24FJ256GA705 PIC24FJ256GB106 PIC24FJ256GB108 PIC24FJ256GB210 PIC24FJ64GA002 PIC24FJ64GA004 PIC24FJ96GA006 PIC24FJ128GA008
- PIC32: PIC32MX110F016B PIC32MX120F032B PIC32MX130F064B PIC32MX150F128B PIC32MX170F256B PIC32MX210F016B PIC32MX220F032B PIC32MX230F064B PIC32MX250F128B PIC32MX270F256B PIC32MX320F032B PIC32MX330F064B
PIC32MX340F128B PIC32MX350F256B PIC32MX360F512L PIC32MX370F512H PIC32MX420F032B PIC32MX430F064B PIC32MX440F128B PIC32MX450F256B PIC32MX460F512L PIC32MX470F512H
AVR Microcontroller Series:
ATtiny4/5/9/10, ATtiny20/40, ATtiny13A, ATtiny2313/4313, ATtiny261/461/861, ATtiny24/44/84, ATtiny26, ATtiny261A/461A/861A, ATtiny167, ATmega2560, ATmega32U4, ATmega8515, ATmega16M1/32M1, ATmega64M1/128M1, ATmega8/48/88/168/328, ATmega16/164/324/644/1284, ATmega16U2/32U2, ATmega1284P, AT90USB82/162, AT90CAN32/64/128.
SAM Microcontroller Series:
SAM3X6E SAM3X8E SAM3A4C SAM3A8C SAM3N0A SAM3N0B SAM3N0C SAM3S2A SAM3S2B SAM3S2C SAM3S4A SAM3S4B SAM3S4C SAM3U1E SAM3U2E SAM3U4E SAM3X4C SAM3X6C SAM3A1C SAM3A3C
dsPIC Digital Signal Controller Series:
dsPIC30F3011 dsPIC30F3012 dsPIC30F3013 dsPIC30F4011 dsPIC30F4012 dsPIC30F4013 dsPIC30F5011 dsPIC30F5012 dsPIC30F5013 dsPIC30F6010 dsPIC30F6011 dsPIC30F6012 dsPIC30F6013 dsPIC30F6014 dsPIC30F6015 dsPIC30F6010A dsPIC30F6011A dsPIC30F6012A dsPIC30F6013A dsPIC30F6014A dsPIC30F6015A dsPIC33FJ12GP202 dsPIC33FJ12GP204 dsPIC33FJ12MC202 dsPIC33FJ12MC204 dsPIC33FJ16GP304 dsPIC33FJ16MC304 dsPIC33FJ32GP302 dsPIC33FJ32GP304 dsPIC33FJ32MC302 dsPIC33FJ32MC304 dsPIC33FJ64GP202 dsPIC33FJ64GP204 dsPIC33FJ64GP502 dsPIC33FJ64GP506 dsPIC33FJ64MC202 dsPIC33FJ64MC204 dsPIC33FJ64MC502 dsPIC33FJ64MC506 dsPIC33FJ128GP202 dsPIC33FJ128GP204 dsPIC33FJ128GP502 dsPIC33FJ128GP506 dsPIC33FJ128MC202 dsPIC33FJ128MC204 dsPIC33FJ128MC502 dsPIC33FJ128MC506

HOLTEK Microelectronics
Holtek HT66 Series:
HT66F0185 HT66F0186 HT66F0187 HT66F0188 HT66F0189 HT66F0190 HT66F0191 HT66F0192 HT66F0193 HT66F0194 HT66F0195 HT66F0196 HT66F0197 HT66F0198 HT66F0199 HT66F0245 HT66F0246 HT66F0247 HT66F0248 HT66F0249 HT66F0250 HT66F0251 HT66F0252 HT66F0253 HT66F0254 HT66F0255 HT66F0256 HT66F0257 HT66F0258 HT66F0259 HT66F0260 HT66F0261 HT66F0262 HT66F0263 HT66F0264 HT66F0265 HT66F0266 HT66F0267 HT66F0268 HT66F0269 HT66F0270 HT66F0271 HT66F0272 HT66F0273 HT66F0274 HT66F0275 HT66F0276 HT66F0277 HT66F0278 HT66F0279 HT66F0280 HT66F0281 HT66F0282 HT66F0283 HT66F0284 HT66F0285 HT66F0286 HT66F0287 HT66F0288 HT66F0289 HT66F0290 HT66F0291 HT66F0292 HT66F0293 HT66F0294 HT66F0295 HT66F0296 HT66F0297 HT66F0298 HT66F0299 HT66F0300 HT66F0301 HT66F0302 HT66F0303 HT66F0304 HT66F0305 HT66F0306 HT66F0307 HT66F0308 HT66F0309 HT66F0310 HT66F0311 HT66F0312 HT66F0313 HT66F0314 HT66F0315 HT66F0316 HT66F0317 HT66F0318 HT66F0319 HT66F0320 HT66F0321 HT66F0322 HT66F0323 HT66F0324 HT66F0325 HT66F0326 HT66F0327 HT66F0328 HT66F0329 HT66F0330 HT66F0331 HT66F0332 HT66F0333 HT66F0334 HT66F0335 HT66F0336 HT66F0337 HT66F0338 HT66F0339 HT66F0340 HT66F0341 HT66F0342 HT66F0343 HT66F0344 HT66F0345 HT66F0346 HT66F0347 HT66F0348 HT66F0349 HT66F0350 HT66F0351 HT66F0352 HT66F0353
Holtek HT45 Series:
HT45F0160 HT45F0161 HT45F0162 HT45F0163 HT45F0164 HT45F0165 HT45F0166 HT45F0167 HT45F0168 HT45F0169 HT45F0170 HT45F0171 HT45F0172 HT45F0173 HT45F0174 HT45F0175 HT45F0176 HT45F0177 HT45F0178 HT45F0179 HT45F0180 HT45F0181 HT45F0182 HT45F0183 HT45F0184 HT45F0185 HT45F0186 HT45F0187 HT45F0188 HT45F0189 HT45F0190 HT45F0191 HT45F0192 HT45F0193 HT45F0194 HT45F0195 HT45F0196 HT45F0197 HT45F0198 HT45F0199 HT45F0200 HT45F0201 HT45F0202 HT45F0203 HT45F0204 HT45F0205 HT45F0206 HT45F0207 HT45F0208 HT45F0209 HT45F0210 HT45F0211 HT45F0212 HT45F0213 HT45F0214 HT45F0215 HT45F0216 HT45F0217 HT45F0218 HT45F0219 HT45F0220 HT45F0221 HT45F0222 HT45F0223 HT45F0224 HT45F0225 HT45F0226 HT45F0227 HT45F0228 HT45F0229 HT45F0230 HT45F0231 HT45F0232 HT45F0233 HT45F0234 HT45F0235 HT45F0236 HT45F0237 HT45F0238 HT45F0239 HT45F0240 HT45F0241 HT45F0242 HT45F0243 HT45F0244 HT45F0245 HT45F0246 HT45F0247 HT45F0248 HT45F0249 HT45F0250 HT45F0251 HT45F0252 HT45F0253 HT45F0254 HT45F0255 HT45F0256 HT45F0257 HT45F0258 HT45F0259 HT45F0260 HT45F0261 HT45F0262 HT45F0263 HT45F0264 HT45F0265 HT45F0266 HT45F0267 HT45F0268 HT45F0269 HT45F0270 HT45F0271 HT45F0272 HT45F0273 HT45F0274 HT45F0275 HT45F0276 HT45F0277 HT45F0278 HT45F0279 HT45F0280 HT45F0281 HT45F0282 HT45F0283 HT45F0284 HT45F0285 HT45F0286 HT45F0287 HT45F0288 HT45F0289 HT45F0290 HT45F0291 HT45F0292 HT45F0293 HT45F0294 HT45F0295 HT45F0296 HT45F0297 HT45F0298 HT45F0299
Holtek HT32 Series:
HT32F0008 HT32F0016 HT32F0032 HT32F0064 HT32F0128 HT32F0256 HT32F0512 HT32F1024 HT32F2048 HT32F5050 HT32F5051 HT32F5052 HT32F5053 HT32F5054 HT32F5055 HT32F5056 HT32F5057 HT32F5058 HT32F5059 HT32F5060 HT32F5061 HT32F5062 HT32F5063 HT32F5064 HT32F5065 HT32F5066 HT32F5067 HT32F5068 HT32F5069 HT32F5070 HT32F5071 HT32F5072 HT32F5073 HT32F5074 HT32F5075 HT32F5076 HT32F5077 HT32F5078 HT32F5079 HT32F5080 HT32F5081 HT32F5082 HT32F5083 HT32F5084 HT32F5085 HT32F5086 HT32F5087 HT32F5088 HT32F5089 HT32F5090 HT32F5091 HT32F5092 HT32F5093 HT32F5094 HT32F5095 HT32F5096 HT32F5097 HT32F5098 HT32F5099 HT32F5100 HT32F5101 HT32F5102 HT32F5103 HT32F5104 HT32F5105 HT32F5106 HT32F5107 HT32F5108 HT32F5109 HT32F5110 HT32F5111 HT32F5112 HT32F5113 HT32F5114 HT32F5115 HT32F5116 HT32F5117 HT32F5118 HT32F5119 HT32F5120 HT32F5121 HT32F5122 HT32F5123 HT32F5124 HT32F5125 HT32F5126 HT32F5127 HT32F5128 HT32F5129 HT32F5130 HT32F5131 HT32F5132 HT32F5133 HT32F5134 HT32F5135 HT32F5136 HT32F5137 HT32F5138 HT32F5139 HT32F5140 HT32F5141 HT32F5142 HT32F5143 HT32F5144 HT32F5145 HT32F5146 HT32F5147 HT32F5148 HT32F5149 HT32F5150 HT32F5151 HT32F5152 HT32F5153 HT32F5154 HT32F5155 HT32F5156 HT32F5157 HT32F5158 HT32F5159 HT32F5160 HT32F5161 HT32F5162 HT32F5163 HT32F5164 HT32F5165 HT32F5166 HT32F5167 HT32F5168 HT32F5169 HT32F5170 HT32F5171 HT32F5172 HT32F5173 HT32F5174 HT32F5175 HT32F5176 HT32F5177 HT32F5178 HT32F5179 HT32F5180 HT32F5181 HT32F5182 HT32F5183 HT32F5184 HT32F5185 HT32F5186 HT32F5187 HT32
Holtek HT54 Series:
HT54F0020 HT54F0040 HT54F0080 HT54F0128 HT54F0256 HT54F0512 HT54F1024 HT54F2048
Holtek HT80 Series:
HT80F064A HT80F128A HT80F256A HT80F512A HT80F0128B HT80F0256B HT80F0512B HT80F1024B HT80F2048B HT80F4096B
Holtek HT90 Series:
HT90F064A HT90F128A HT90F256A HT90F512A HT90F0128B HT90F0256B HT90F0512B HT90F1024B HT90F2048B HT90F4096B
Holtek HT48 Series:
HT48R0011 HT48R0021 HT48R0041 HT48R0042 HT48R0081 HT48R0181 HT48R0281 HT48R0381 HT48R0681 HT48R0781 HT48R0881 HT48R1081 HT48R2081 HT48R3081 HT48R4081 HT48R6081 HT48R7081 HT48R8081
Holtek HT49 Series:
HT49C40 HT49C60 HT49C80 HT49C00 HT49C10 HT49C20 HT49C30
Holtek HT93 Series:
HT93LC46 HT93LC66 HT93LC86 HT93LC46A HT93LC66A HT93LC86A HT93LC96 HT93LC46B HT93LC66B HT93LC86B HT93LC96B HT93C66 HT93C46 HT93C86

Winbond Integrated Circuit
W25X Series:
W25X10 W25X20 W25X40 W25X80 W25X16 W25X32 W25X64 W25X128 W25X256
W26X Series:
W26X10 W26X20 W26X40 W26X80 W26X16 W26X32 W26X64 W26X128 W26X256
W77E series: W77E058A W77E058 W77E51 W77E516A W77E516 W77E52 W77E532 W77E532A W77E54 W77E58 W77E58A W77I058A 77L058 W77L516A W77LE58 W77IE58 W77L058A W77L516A W77L532A W77LE516 W77LE532
W78E series:
W78E51 W78E51B W78E52B W78E54 W78E52 W78E54B W78E58 W78E516 W78E051A W78E58B W78E62 W78E65 W78E516B W78E051B W78E65B W78E051C W78E052A W78E052C W78E054A W78E052B W78E054B W78E054C W78E058B W78E065A W78E058A W78E365 W78E365A W78E378E W78E51 W78E378 W78E516B W78E51B W78E52 W78E52B W78E51C W78E52C W78E54 W78E54C W78E58 W78E54B W78E58B W78E62 W78E858 W78ERD2 W78E65 W78ERD2A W78E051DDG W78E051DLG W78E051DFG W78E051DPG W78E052DDG W78E052DLG W78E052DPG W78E052DFG W78E054DDG W78E054DFG W78E054DPG W78E058DDG W78E054DLG W78E058DFG W78E058DPG W78E065 W78E058DLG W78E354 W78E374B W78E516DDG W78E378P W78E516DFG W78E516DLG W78E62B W78E516DPG
W78L series:
W78L052C, W78L052D, W78L052DD, W78L052DQ, W78L052DZ, W78L052G, W78L052GD, W78L052GQ, W78L052GZ, W78L052S, W78L052SD, W78L052SQ, W78L052SZ, W78L052V, W78L052VD, W78L052VQ, W78L052VZ, W78L052W, W78L052WD, W78L052WQ, W78L052WZ, W78L052X, W78L052XD, W78L052XQ, W78L052XZ, W78L052Y, W78L052YD, W78L052YQ, W78L052YZ, W78L052Z, W78L052ZD, W78L052ZQ, W78L052ZZ, W78L05A, W78L05AD, W78L05AQ, W78L05AZ, W78L05S, W78L05SD, W78L05SQ, W78L05SZ, W78L05V, W78L05VD, W78L05VQ, W78L05VZ, W78L05W, W78L05WD, W78L05WQ, W78L05WZ, W78L05X, W78L05XD, W78L05XQ, W78L05XZ, W78L05Y, W78L05YD, W78L05YQ, W78L05YZ, W78L05Z, W78L05ZD, W78L05ZQ, W78L05ZZ, W78LE516, W78LE516D, W78LE58B, W78LE58B-24, W78LE58B-40, W78LE58B-24/3, W78LE58B-40/3, W78LE58D, W78LE58DD, W78LE58P, W78LE58PD, W78LE58S, W78LE58SD, W78LE58V, W78LE58VD, W78LE58X, W78LE58XD, W78LE58Y, W78LE58YD, W78LE58Z, W78LE58ZD, W78LE516P, W78LE516PD, W78LE516S, W78LE516SD, W78LE516V, W78LE516VD, W78LE516X, W78LE516XD, W78LE516Y, W78LE516YD, W78LE516Z, W78LE516ZD.
W79E series:
W79E2051, W79E2051A, W79E2051B, W79E2051K, W79E2051KB, W79E2051KX, W79E2061, W79E2061A, W79E2061B, W79E2061K, W79E2061KB, W79E2061KX, W79E451, W79E451A, W79E451B, W79E451K, W79E451KB, W79E451KX, W79E532, W79E532A, W79E532B, W79E532K, W79E532KB, W79E532KX, W79E58, W79E58A, W79E58B, W79E58K, W79E58KB, W79E58KX, W79E65, W79E65A, W79E65B, W79E65K, W79E65KB, W79E65KX, W79E8251, W79E8251A, W79E8251B, W79E8251K, W79E8251KB, W79E8251KX, W79E8351, W79E8351A, W79E8351B, W79E8351K, W79E8351KB, W79E8351KX, W79EGD0AB, W79EGD0BB, W79EGD0KB, W79EGD0KX, W79EGD0KB-SPI, W79EKB0AC, W79EKB0BC, W79EKB0KC, W79EKB0KX.
W79L series:
W79L064A, W79L064S, W79L064AD, W79L064SD, W79L064AQ, W79L064SQ, W79L064AN, W79L064SN, W79L064AP, W79L064SP, W79L064APR, W79L064SPR, W79L064AS, W79L064SS, W79L064ASP, W79L064SSP, W79L064AW, W79L064SW, W79L064AWP, W79L064SWP, W79L064AWR, W79L064SWR, W79L064AT, W79L064ST, W79L064ATP, W79L064STP, W79L064ATR, W79L064STR, W79L064AX, W79L064SX, W79L064AXP, W79L064SXP, W79L064AXR, W79L064SXR, W79L064AY, W79L064SY, W79L064AYP, W79L064SYP, W79L064AYR, W79L064SYR, W79L064AZ, W79L064SZ, W79L064AZP, W79L064SZP, W79L064AZR, W79L064SZR, W79L065A, W79L065S, W79L065AD, W79L065SD, W79L065AQ, W79L065SQ, W79L065AN, W79L065SN, W79L065AP, W79L065SP, W79L065APR, W79L065SPR, W79L065AS, W79L065SS, W79L065ASP, W79L065SSP, W79L065AW, W79L065SW, W79L065AWP, W79L065SWP, W79L065AWR, W79L065SWR, W79L065AT, W79L065ST, W79L065ATP, W79L065STP, W79L065ATR, W79L065STR, W79L065AX, W79L065SX, W79L065AXP, W79L065SXP, W79L065AXR, W79L065SXR, W79L065AY, W79L065SY, W79L065AYP, W79L065SYP, W79L065AYR, W79L065SYR, W79L065AZ, W79L065SZ, W79L065AZP, W79L065SZP, W79L065AZR, W79L065SZR.
W83L series:
W83L951G, W83L951GAW, W83L951GAW1, W83L951GAW2, W83L951GAZ, W83L951GB, W83L951GBW, W83L951GBW1, W83L951GBW2, W83L951GBZ, W83L951GG, W83L951GGW, W83L951GGW1, W83L951GGW2, W83L951GGZ, W83L951GH, W83L951GHW, W83L951GHW1, W83L951GHW2, W83L951GHZ, W83L951GI, W83L951GIW, W83L951GIW1, W83L951GIW2, W83L951GIZ, W83L951GM, W83L951GMW, W83L951GMW1, W83L951GMW2, W83L951GMZ, W83L951GV, W83L951GVW, W83L951GVW1, W83L951GVW2, W83L951GVZ, W83L951GZ, W83L951HG, W83L951HGZ, W83L951HI, W83L951HIZ, W83L952G, W83L952GAW, W83L952GAW1, W83L952GAW2, W83L952GAZ, W83L952GB, W83L952GBW, W83L952GBW1, W83L952GBW2, W83L952GBZ, W83L952GG, W83L952GGW, W83L952GGW1, W83L952GGW2, W83L952GGZ, W83L952GH, W83L952GHW, W83L952GHW1, W83L952GHW2, W83L952GHZ, W83L952GI, W83L952GIW, W83L952GIW1, W83L952GIW2, W83L952GIZ, W83L952GM, W83L952GMW, W83L952GMW1, W83L952GMW2, W83L952GMZ, W83L952GV, W83L952GVW, W83L952GVW1, W83L952GVW2, W83L952GVZ, W83L952GZ, W83L952HG, W83L952HGZ, W83L952HI, W83L952HIZ.

SST Microcontroller
SST89C Series:
SST89C52, SST89C54, SST89C58, SST89C60, SST89C61, SST89C62, SST89C64, SST89C664, SST89C516, SST89C516RD, SST89C516RD2, SST89C516RD2-40-C-NJE, SST89C516RD2-40-C-PIE, SST89C516RD2-40-C-TQJE, SST89C516RD2-40-C-TQPIE, SST89C516RD2-40-C-UPJE, SST89C516RD2-40-C-UUPIE, SST89C516RD2-40-C-WJE, SST89C516RD2-40-C-WPIE, SST89C516RD2-40-C-XQJE, SST89C516RD2-40-C-XQPIE, SST89C516RD2-40-C-XUJE, SST89C516RD2-40-C-XUPIE, SST89C516RD2-40-C-ZQJE, SST89C516RD2-40-C-ZQPIE, SST89C516RD2-40-C-ZUJE, SST89C516RD2-40-C-ZUPIE, SST89C516RD2-40-I-NJE, SST89C516RD2-40-I-PIE, SST89C516RD2-40-I-TQJE, SST89C516RD2-40-I-TQPIE, SST89C516RD2-40-I-UPJE, SST89C516RD2-40-I-UUPIE, SST89C516RD2-40-I-WJE, SST89C516RD2-40-I-WPIE, SST89C516RD2-40-I-XQJE, SST89C516RD2-40-I-XQPIE, SST89C516RD2-40-I-XUJE, SST89C516RD2-40-I-XUPIE, SST89C516RD2-40-I-ZQJE, SST89C516RD2-40-I-ZQPIE, SST89C516RD2-40-I-ZUJE, SST89C516RD2-40-I-ZUPIE, SST89C516RD2-40-J-NJE, SST89C516RD2-40-J-PIE, SST89C516RD2-40-J-TQJE, SST89C516RD2-40-J-TQPIE, SST89C516RD2-40-J-UPJE, SST89C516RD2-40-J-UUPIE, SST89C516RD2-40-J-WJE, SST89C516RD2-40-J-WPIE, SST89C516RD2-40-J-XQJE, SST89C516RD2-40-J-XQPIE, SST89C516RD2-40-J-XUJE, SST89C516RD2-40-J-XUPIE, SST89C516RD2-40-J-ZQJE, SST89C516RD2-40-J-ZQPIE, SST89C516RD2-40-J-ZUJE, SST89C516RD2-40-J-ZUPIE, SST89C516RD2-40-Q-NJE, SST89C516RD2-40-Q-PIE, SST89C516RD2-40-Q-TQJE, SST89C516RD2-40-Q-TQPIE, SST89C516RD2-40-Q-UPJE, SST89C516
SST89E Series:
SST89E516RD, SST89E516RD-40-C-NJE, SST89E516RD-40-C-PIE, SST89E516RD-40-C-TQJE, SST89E516RD-40-C-TQPIE, SST89E516RD-40-C-UPJE, SST89E516RD-40-C-UUPIE, SST89E516RD-40-C-WJE, SST89E516RD-40-C-WPIE, SST89E516RD-40-C-XQJE, SST89E516RD-40-C-XQPIE, SST89E516RD-40-C-XUJE, SST89E516RD-40-C-XUPIE, SST89E516RD-40-C-ZQJE, SST89E516RD-40-C-ZQPIE, SST89E516RD-40-C-ZUJE, SST89E516RD-40-C-ZUPIE, SST89E516RD-40-I-NJE, SST89E516RD-40-I-PIE, SST89E516RD-40-I-TQJE, SST89E516RD-40-I-TQPIE, SST89E516RD-40-I-UPJE, SST89E516RD-40-I-UUPIE, SST89E516RD-40-I-WJE, SST89E516RD-40-I-WPIE, SST89E516RD-40-I-XQJE, SST89E516RD-40-I-XQPIE, SST89E516RD-40-I-XUJE, SST89E516RD-40-I-XUPIE, SST89E516RD-40-I-ZQJE, SST89E516RD-40-I-ZQPIE, SST89E516RD-40-I-ZUJE, SST89E516RD-40-I-ZUPIE, SST89E516RD-40-J-NJE, SST89E516RD-40-J-PIE, SST89E516RD-40-J-TQJE, SST89E516RD-40-J-TQPIE, SST89E516RD-40-J-UPJE, SST89E516RD-40-J-UUPIE, SST89E516RD-40-J-WJE, SST89E516RD-40-J-WPIE, SST89E516RD-40-J-XQJE, SST89E516RD-40-J-XQPIE, SST89E516RD-40-J-XUJE, SST89E516RD-40-J-XUPIE, SST89E516RD-40-J-ZQJE, SST89E516RD-40-J-ZQPIE, SST89E516RD-40-J-ZUJE, SST89E516RD-40-J-ZUPIE, SST89E516RD-40-Q-NJE, SST89E516RD-40-Q-PIE, SST89E516RD-40-Q-TQJE, SST89E516RD-40-Q-TQPIE, SST89E516RD-40-Q-UPJE, SST89E516RD-40-Q-UUPIE, SST89E516RD-40-Q-WJE, SST89E516RD-40-Q-WPIE, SST89E516RD-40-Q-XQJE, SST89E516RD-40-Q-XQPIE, SST89E516RD-40-Q-XUJE, SST89E516RD-40-Q-XUPIE, SST89E516RD-40-Q-ZQJE, SST89E516RD-40-Q-ZQPIE
SST89V Series:
SST89V564RD SST39VF1682 SST39VF6401 SST39VF6401B SST39VF3201 SST39VF3202 SST89V516RD SST89V554RC SST39VF1602 SST89V52RD2 SST89V52RD SST89V516RD2 SST89V54RD2 SST39VF6402 SST39VF6402B SST89V58RD2 SST39VF1601

SyncMOS Microcontroller
MSU Series:
MSU1958 MSU2964 MSU2952 MSU2958
SM29 Series:
SM2951 SM2952 SM2958 SM2964 SM2954 SM2965
SM59 Series:
SM7908 SM79164 SM79164L SM79108 SM79164V SM7964 SM7932
S29C Series:
S29C51001B S29C51002B S29C31002B S29C51001T S29C31004B S29C31002T S29C51004B S29C31004T S29C51002T S29C31001B S29C51004T S29C31001T
F29C Series:
F29C31400T F29LC51001 F29C51002T F29C51004T F29C51000T F29C51002B F29C51001T F29C51001B F29C51004B F29LC51002 F29C31004T F29C51002T F29C31004B F29C51000B F29C51004T F29C51001T F29C61400T F29C31004B
SM59 Series:
SM89516 SM8951 SM8958 SM89516B SM8952AL SM8952 SM8952B SM8951AL SM8951B SM8958AL SM89516AL SM89516A SM8954AL SM8951A SM89S16R1C SM8954 SM8954A SM8952L SM8958L SM8952A SM8951L SM89T16R1L SM89T08R1L SM8954B SM89T04R1L SM89516L SM8958B SM8954BL SM8952BL SM89T16R1C SM89T08R1C SM8951BL SM89T04R1C SM89516L SM5964D0 SM5916C SM5964 SM5912C SM5912L SM5964AC SM59D02G2C SM59D03G2C SM59R08A2 SM5964A SM5964D0A SM59128C SM5916L SM59128L SM59D04G2C SM59264 SM5964C SM5964AL SM59164 SM5964D1A SM59D03G2L SM59D04G2L SM59D02G2L
Silicon-Labs Microcontroller
Silabs F Series:
SILF023 SILF041 SILF015 SILF006 SILF065 SILF330 SILF520 SILF127 SILF360 SILF017 SILF530 SILF121 SILF523 SILF305 SILF313 SILF337 SILF132 SILF124 SILF207 SILF244 SILF071 SILF038 SILF056 SILF233 SILF023 SILF017 SILF004 SILF363 SILF301 SILF313 SILF035 SILF314 SILF533 SILF334 SILF130 SILF345 SILF005 SILF044 SILF534 SILF041 SILF537 SILF346 SILF062 SILF315 SILF024 SILF023 SILF521 SILF337 SILF347 SILF015 SILF364 SILF526 SILF014 SILF341 SILF332 SILF070 SILF044 SILF341 SILF930 SILF132 SILF233 SILF522 SILF364 SILF067 SILF523 SILF526 SILF367 SILF332 SILF316 SILF920 SILF240 SILF343 SILF044 SILF523 SILF361 SILF362 SILF060 SILF538 SILF338 SILF367 SILF520 SILF230 SILF923 SILF534 SILF343 SILF322 SILF330 SILF127 SILF061 SILF332 SILF524 SILF014 SILF346 SILF535 SILF920 SILF016 SILF317 SILF535 SILF522 SILF126 SILF364 SILF044 SILF122 SILF526 SILF924 SILF064 SILF316 SILF064 SILF532 SILF337 SILF344 SILF920 SILF126 SILF930 SILF341 SILF343 SILF526 SILF044 SILF012 SILF334 SILF533 SILF347 SILF521 SILF924 SILF327 SILF300 SILF014 SILF527 SILF532 SILF345 SILF331 SILF061 SILF338 SILF536 SILF318 SILF320 SILF345 SILF347 SILF343 SILF535 SILF038 SILF536 SILF335 SILF064 SILF066 SILF017 SILF315 SILF342 SILF346 SILF065 SILF311 SILF316 SILF920 SILF018 SILF336 SILF244 SILF920 SILF343 SILF534 SILF923 SILF336 SILF017 SILF123 SILF061 SILF536 SILF920 SILF348 SILF044 SILF065 SILF920 SILF125 SILF541 SILF122 SILF530 SILF016 SILF015 SILF345 SILF014 SILF344 SILF366 SILF923 SILF362 SILF926 SILF053 SILF064 SILF064 SILF064 SILF335 SILF923 SILF064 SILF062 SILF018 SILF017 SILF064 SILF064 SILF014 SILF316 SILF127 SILF920 SILF044 SILF537 SILF343 SILF534 SILF037 SILF312 SILF233 SILF924 SILF536 SILF070 SILF348 SILF333 SILF317 SILF361 SILF347 SILF930 SILF536 SILF327 SILF923 SILF366 SILF920 SILF530 SILF122 SILF346 SILF071 SILF017 SILF315 SILF537 SILF343 SILF061 SILF018 SILF523 SILF536 SILF920 SILF530 SILF316 SILF332 SILF920 SILF344 SILF310 SILF015 SILF333 SILF312 SILF321 SILF310 SILF527 SILF334 SILF923 SILF345
Silabs T Series:
SILT600 SILT601 SILT602 SILT603 SILT604 SILT605 SILT610 SILT611 SILT612 SILT613 SILT614 SILT615 SILT616 SILT617 SILT630 SILT631 SILT632 SILT633 SILT634 SILT635

Texas-Instruments Microcontrollers
TMS320 Series:
TMS320F28052 TMS320C2811 TMS320F2812PGFA TMS320C6713BGDP300 TMS320C31PQL4 TMS320F2812 TMS320C31PQL40 TMS320F206PZ TMS320LF2812 TMS320LF28335PGFA TMS320C28342 TMS320F28067 TMS320F2811 TMS320F28064 TMS320LF28335 TMS320C6713BPYP200 TMS320C28343 TMS320C6203BGNY TMS320F28335 TMS320LF2802-60 TMS320C6701GJC150 TMS320F2810PBKA TMS320F2812 TMS320C28344 TMS320C6701GJC TMS320C6713BGDPA200 TMS320C6202GJL TMS320F28335PGFA TMS320F2810 TMS320F28063 TMS320F2808PZA TMS320F28026 TMS320F2812 TMS320C542PGE2-40 TMS320C25FNL-50 TMS320LF2812pgfa TMS320F2402A TMS320C30GEL TMS320LF2407APGES TMS320F243PGE TMS320C25FNA TMS320LF2806 TMS320F28022 TMS320C25FNL33 TMS320LF2806PZA TMS320C2812 TMS320C25FNL TMS320F2808 TMS320C25F2L TMS320F2812PGFA TMS320C28345 TMS320F28021 TMS320LF2407APGEA TMS320C51PZ57 TMS320C2810 TMS320C6713BGDPA30 TMS320F2809 TMS320F28050 TMS320F28069 TMS320C28346 TMS320F28054 TMS320LF2401AVFA TMS320F2407A TMS320F2806PZQ TMS320F28044 TMS320VC5416PGE160 TMS320LF2406 TMS320F28052 TMS320C14FNL TMS320C2812 TMS320F2802 TMS320F28235 TMS320C32PCM60 TMS320F28334 TMS320F2812 TMS320F28021 TMS320F2406APZA TMS320C28341 TMS320F2406A TMS320VC5506PGE TMS320F28065 TMS320LF2406PIA TMS320C2811 TMS320F2812 TMS320C28341 TMS320F2812PGFA TMS320C28342 TMS320C28344 TMS320F28027 TMS320F2812 TMS320C28345 TMS320LF2812 TMS320C28346 TMS320C28343 TMS320F2812 TMS320F2810 TMS320F2801PZA TMS320C2810 TMS320F2808PZA TMS320C6701GJC150 TMS320C2811 TMS320F28051 TMS320VC5506ZHH TMS320F2407APGEA TMS320VC5410PGE TMS320F2812 TMS320F2812 TMS320F2812 TMS320F2806
TMS Series:
TMS9980A TMS470R1VF4B8PZA TMS626162 TMS570LS10116 TMS55160 TMS664814 TMS6644148 TMS470R1VF67AGJZA TMS9927 TMS6641648 TMS626812B TMS70C82 TMS470R1VF689 TMS470R1VF67AGJZT TMS55171 TMS626162A TMS9927JL TMS570LS10216 TMS5502NL TMS66481410 TMS470R1VF48BPGET TMS470R1VF348EPZ-T TMS99534A TMS664164 TMS55165 TMSDC6726BRFPA225 TMS9981 TMS55176 TMSDC6727BZDHA250 TMS70C02 TMS9980 TMS626812 TMS63D/S-24 TMS55170 TMS87C257 TMS9914 TMS9927NL TMS55166 TMS66441410 TMSDC6727BGDHA250 TMS55175 TMS4C2972 TMSDC6722BRFPA225 TMSDC6727BGDHA250 TMS470R1VF67AGJZQ TMS470R1VF4B8PZT TMS470R1VF48CPGEQ TMS570LS20206 TMS570LS10206 TMS57014ADWBLE TMS5501NL TMS470R1VF48BPGEQ TMS9900 TMS99532A TMSDC6727BZDHA250 TMS570LS20216 TMSDC6701GJC16719V TMSDC6727BGDHA250 TMSDC6701 TMS5001NL TMS9995NL TMS99531 TMS9981 TMS9927NL TMS470R1VF48CPGEQ TMS470R1VF67A TMS470R1VF48B TMS470R1VF67AGJZA TMS470R1VF4B8 TMS470R1VF348APZQ TMS470R1VF348PZA TMS470R1VF448PZ-T TMS470R1VF348EPZA TMS470R1VF348PZQ TMS470R1VF448PZQ TMS470R1VF348APZ-T TMS55161 TMS66416410 TMSDC6727BZDHA250 TMS9927 TMS570LS31 TMS55160 TMS9980A TMSDC6727BGDHA250 TMS55170 TMS55165 TMS70C82 TMS470R1VF689 TMS55175 TMS664814 TMS470R1VF67AGJZT TMS626162A TMS470R1VF48CPGEA TMS470R1VF4B8PZQ TMS470R1VF48BPGEA TMS470R1VF348PZA TMS626812B TMS6644148A TMSDC6727BGDHA250 TMS5501NL TMS570LS10216 TMS9927JL TMS5502NL TMS6641648A TMS55171 TMS570LS10106 TMS63D/S-24 TMS55176 TMS470R1VF448PZA TMS664414 TMS9980 TMS626812 TMS55166 TMS70C02 TMS66481410 TMSDC6727BGDHA250 TMS87C257 TMS9981

STCmicro Microcontrollers
STC89C Series:
STC89C58RD STC89C51RC STC89C53RC STC89C52RC STC89C54RD+ STC89C516RD STC89C58RD+ STC89C516RD+
STC89LE/LV Series:
STC89LE556X2 STC89LE54RD+ STC89LE516RD+ STC89LE516X2 STC89LE58AD STC89LE516AD STC89LE56AD STC89LE52RC STC89LE556AD STC89LE51RC STC89LV516RD STC89LE54AD STC89LE53RC STC89LV58RD STC89LE58RD+
STC90C Series:
STC90C514AD STC90C54AD STC90LE54AD STC90C58RD+ STC90LE51RC STC90LE58RD+ STC90LE58AD STC90C510RD+ STC90C52AD STC90LE514RD+ STC90LE512RD+ STC90C516RD+ STC90LE516AD STC90C514RD+ STC90LE52AD STC90LE516RD+ STC90C52RC STC90C53RC STC90LE53RC STC90C516AD STC90C58AD STC90C512RD+ STC90C54RD+ STC90LE510RD+ STC90LE54RD+ STC90C51RC STC90LE52RC STC90LE514AD STC90LE58RD+ STC90LE512RD+ STC90C514AD
STC10F Series:
STC10F04 STC10F08 STC10F04XE STC10F08XE STC10F12XE STC10F12 STC10F14X
STC11F Series:
STC11F01E STC11F03E STC11F02E STC11F04E IAP11F06 STC11F05E STC11F60XE STC11F52XE STC11F56XE STC11F48XE STC11F32XE STC11F40XE STC11F20XE STC11F08XE STC11F16XE STC11F62X
STC12C / STC12LE Series:
STC12C5624AD STC12C5A48AD STC12C5412 STC12C5204AD STC12C5404 STC12C5604AD STC12C5A08S2 STC12LE5A08S2 STC12C5205AD STC12C5A16AD STC12LE5A40S2 STC12C5620AD STC12LE5A32S2 STC12C5402AD STC12C5A32AD STC12C5628AD STC12C5410 STC12C5408AD STC12C5616AD STC12C5203AD STC12C4052 STC12C5608AD STC12LE5620AD STC12C5052 STC12C5600AD STC12LE5628AD STC12C5620 STC12C5612AD STC12C5406AD STC12C5206AD STC12C5408 STC12LE5202AD STC12C5A56AD STC12C5202AD STC12LE5A56S2 STC12LE5A08AD STC12C5A40S2 STC12C5612 STC12C5201AD STC12C5624 STC12C5A48S2 STC12LE5A52S2 STC12C5410AD STC12C5A60S2 STC12LE5204AD STC12C5206 STC12C5A52S2 STC12LE5624AD STC12C5616 STC12LE5A40AD STC12C5412RD STC12C5402 STC12C5A56S2 STC12C5600 STC12LE5205AD STC12C5630AD STC12C5406 STC12LE5203AD STC12C5A16S2 STC12C5612RD STC12C5205 STC12C5408S2 STC12LE5A60AD STC12LE5206AD STC12C5A52AD STC12LE5A16S2 STC12C5204 STC12LE5A52AD STC12C5404AD STC12C5203 STC12LE5604AD STC12LE5201AD STC12C5608 STC12C5202 STC12C5201 STC12C5A48 STC12C5206AD STC12LE5628AD STC12C5628 STC12C5620S2 STC12LE5620 STC12C5402S2 STC12C5202S2 STC12LE5A60S2 STC12LE5A48AD STC12LE5A32AD STC12C5604 STC12LE5616AD STC12LE5A16AD STC12C5616S2 STC12C5406S2 STC12LE5624 STC12C5624S2 STC12C5400AD STC12LE5A32S2 STC12C5205S2 STC12LE5A08S2 STC12C5400 STC12C5628S2 STC12C5616AD STC12LE5A56AD STC12C5A60AD STC12C5A32S2 STC12C540
STC15F Series:
STC15F2K60S IAP15F105W IRC15F107W STC15F2K61S IAP15F2K61S2 STC15F2K48AS IRC15F107W STC15F2K63S2 STC15F2K56S2 STC15F2K40S2 STC15F2K16S2 STC15F2K32S2 STC15F101W STC15F2K61S STC15F2K48S2 STC15F100W STC15F104W STC15F2K24AS STC15F102W
STC15L Series:
STC15L100W STC15L102W STC15L101W STC15L104W STC15L2K16S2 STC15L2K08S2 STC15L2K32S2 STC15L2K48S2 STC15L2K40S2 STC15L2K56S2 IAP15L105W STC15L2K60S2 IAP15L2K61S2
STC15W Series:
STC15W102 STC15W404AS STC15W408AS STC15W410S STC15W1K16PWM STC15W1K08PWM STC15W101 STC15W201S STC15W202S STC15W1K24S STC15W408S STC15W413AS STC15W100 STC15W2K16S STC15W404S STC15W4K40S4 STC15W4K16S4 STC15W4K56S4 STC15W4K32S4 STC15W1K16S STC15W4K48S4 STC15W204S STC15W401AS STC15W203S STC15W104

Xilinx Microcontrollers
XC Series:
XC3S50 XC3S200 XC3S400 XC3S700 XC3S1400 XC3S2000 XC3S4000 XC3S5000 XC3S700A XC3S1400A XC3S2000A XC3S4000A XC3S5000A XC3S700AN XC3S1400AN XC3S2000AN XC3S4000AN XC3S5000AN XC3S700AAN XC3S1400AAN XC3S2000AAN XC3S4000AAN XC3S5000AAN XC3S1500 XC3S2500 XC3S3500 XC3S50A XC3S200A XC3S400A XC3S700AAN XC3S1400AAN XC3S2000AAN XC3S4000AAN XC3S5000AAN XC3S1000 XC3S1500A XC3S2000A XC3S4000A XC3S5000A XC3S1000A XC3S1500AN XC3S2000AN XC3S4000AN XC3S5000AN XC3S1000AN XC3S2000AF XC3S4000AF XC3S5000AF XC3S700AF XC3S200AN XC3S400AN XC3S500AN XC3S700AFG676 XC3S700AN-4FGG676I XC3S1000-4FT256C XC3S1000-4FTG256C XC3S1000-4FG320C XC3S1000-4FG320I XC3S1000-4FG456C XC3S1000-4FG456I XC3S1000-4FG676C XC3S1000-4FG676I XC3S1000-4FTG256I XC3S1000-4FTG320C XC3S1000-4FTG320I XC3S1000-4FTG456C XC3S1000-4FTG456I XC3S1000-4FG320I XC3S1000-4FG456I XC3S1000-4FG676I XC3S1000-5FT256C XC3S1000-5FTG256C XC3S1000-5FG320C XC3S1000-5FG320I XC3S1000-5FG456C XC3S1000-5FG456I XC3S1000-5FG676C XC3S1000-5FG676I XC3S1000-5FTG256I XC3S1000-5FTG320C XC3S1000-5FTG320I XC3S1000-5FTG456C XC3S1000-5FTG456I XC3S1000-5FG320I XC3S1000-5FG456I XC3S1000-5FG676I XC3S1000A-4FT256C XC3S1000A-4FTG256C XC3S1000A-4FG320C XC3S1000A-4FG320I XC3S1000A-4FG456C XC3S1000A-4FG456I XC3S1000A-4FG676C XC3S1000A-4FG676I XC3S1000A-4FTG256I XC3S1000A-4FTG320C XC3S1000A-4FT

FUJITSU Microcontrollers
MB90F3 Series:
MB90F335 MB90F334 MB90F337 MB90F343 MB90F342 MB90F345 MB90F347 MB90F346 MB90F349 MB90F351 MB90F394HA MB90F352 MB90F357 MB90F356
MB90F4 Series:
MB90F423 MB90MF408 MB90F428 MB90F438L MB90F443G MB90F439 MB90F456 MB90F455 MB90F457 MB90F463 MB90F462 MB90F481B MB90F488B MB90F482B MB90F489B MB90F498G MB90F497G
MB90F5 Series:
MB90F548G MB90F543G MB90F549G MB90F562 MB90F546G MB90F568 MB90F594G MB90F591G MB90F598G
MB90F8 Series:
MB90F897 MB90F804 MB90F822B MB90F809 MB90F823B MB90F867E MB90F828B MB90F882A MB90F883BH MB90F883B MB90F883C MB90F884BH MB90F884B MB90F884C
MB90F Series:
MB90F548G MB90F543G MB90F549G MB90F562 MB90F546G MB90F568 MB90F594G MB90F591G MB90F598G
MB96F Series:
MB96F347A/R/Y MB96F343D/F MB96F346A/R/Y MB96F313A/R/Y MB96F388H/T MB96F385R/Y MB96F379R/Y MB96F355A/R/Y MB96F675AA/RA MB96F346A/R/Y MB96F356A/R/Y MB96F387R/Y MB96F385R/Y MB96F346A/R/Y MB96F395R/Y MB96F673AA/RA MB96F386R/Y MB96F326A/R/Y MB96F348A/R/Y MB96F313A/R/Y MB96F347A/R/Y MB96F338R/U/Y MB96F348C/H/T MB96F683AA/RA MB96F343D/F MB96F345D/F MB96F673AA/RA MB96F346A/R/Y MB96F388H/T MB96F353A/R MB96F379R/Y MB96F386R/Y MB96F387R/Y MB96F318R/Y

NXP Microcontrollers
P87C5 Series:
P87C51 P87C54 P87C552 P87C54X2 P87C52 P87C58 P87C52X2BN P87C52X2BN P87C51RA+ P87C58X2 P87C52UBAA P87C51FA P87C51FB P87C54UBAA P87C51X2 P87C51RC2 P87C51FC P87C51MB2 P87C51RB+ P87C51RB2 P87C51RA2 P87C51RC+ P87C51RD2 P87C52X2 P87C51RD+ P87C554 P87C51X2BA P87C557E8 P87C591 P87C592
P87C Series:
P87C654X2 P87C451 P87C661X2 P87C453 P87C749 P87C748 P87C750 P87C751 P87C752 P87C660X2
P89C Series:
P89C138 P89C60X2BA P89C238 P89C60X2 P89C660H P89C61X2 P89C662H P89C668H P89C664H P89C669 P89C739 P89C738
P89V Series:
P89LV51RC2 P89LV51RB2 P89LV51RD2 P89V51RB2 P89V51RB2 P89V51RC2 P89V51RD2 P89V51RC2 P89V660 P89V664 P89V662
P89C5 Series:
P89C54X2BA P89C51RB2H P89C51RD2H P89C52U P89C51RB P89C54B P89C51RA+ P89C51RA2 P89C58B P89C58U P89C52B P89C51RD2 P89C51RC2H P89C51RB+ P89C51RA2BN P89C51RD2B P89C51RC2 P89C58X2FN P89C138 P89C52X2 P89C54U P89C51RA2BN P89C51X2 P89C51U P89C60X2BA P89C52B P89C51RC P89C739 P89C58X2 P89C51RD+ P89C51RD2F P89C238 P89C54B P89C51RD2 P89C51RC P89C51RB2 P89C51RD2H P89C669 P89C60X2 P89C52X2 P89C662H P89C51RA2 P89C58 P89C58X2 P89C51RC+ P89C51RA2BN P89C51RD2 P89C738 P89C61X2 P89C668H P89C660H P89C664H
P87LPC Series:
P87LPC779 P87LPC76X P87LPC760 P87LPC759 P87LPC761 P87LPC764 P87LPC762 P87LPC767 P87LPC769 P87LPC768 P87LPC778
P89LPC Series:
P89LPC779 P89LPC901 P89LPC902 P89LPC903 P89LPC904 P89LPC906 P89LPC907 P89LPC908 P89LPC9102 P89LPC9103 P89LPC9107 P89LPC912 P89LPC913 P89LPC914 P89LPC915 P89LPC916 P89LPC917 P89LPC920 P89LPC9201 P89LPC921 P89LPC9211 P89LPC922 P89LPC9221 P89LPC922A1 P89LPC924 P89LPC9241 P89LPC925 P89LPC9251 P89LPC930 P89LPC9301 P89LPC931 P89LPC9311 P89LPC931A1 P89LPC932 P89LPC9321 P89LPC932A1 P89LPC933 P89LPC9331 P89LPC934 P89LPC9341 P89LPC935 P89LPC9351 P89LPC936 P89LPC9361 P89LPC938 P89LPC9401 P89LPC9402 P89LPC9408 P89LPC952 P89LPC954 P89LPC970 P89LPC971 P89LPC972 P89LPC980 P89LPC982
LPC Series:
LPC2124 LPC1766 LPC2468 LPC1857 LPC1758 LPC1772 LPC2109 LPC2102 LPC3250 LPC2132 LPC2106 LPC2101 LPC2362 LPC2388 LPC1113 LPC2136 LPC1788 LPC11E12/201 LPC1316 LPC1111 LPC11E36/501 LPC11U14/201 LPC2157 LPC1342 LPC2470 LPC3130 LPC2148 LPC3200 LPC2364 LPC1764 LPC11A13/201 LPC4074 LPC1767 LPC1345 LPC1317 LPC4330 LPC2104 LPC1785 LPC3220 LPC1114 LPC1810 LPC3254 LPC2103 LPC2105 LPC2129 LPC3252 LPC11C12/301 LPC11U37/401 LPC11A04 LPC11C22/301 LPC11U13/201 LPC1111/002 LPC4088 LPC11A14/301 LPC1114/333 LPC11C14/301 LPC11U35/501 LPC11A11/001 LPC1114/301 LPC11U24/401 LPC1112/202 LPC11U12/201 LPC11E13/301 LPC2292 LPC3180 LPC2460 LPC2124 LPC2131 LPC1311 LPC2124 LPC2378 LPC1113 LPC2294 LPC3152 LPC1830 LPC2141 LPC2119 LPC2146 LPC1313 LPC2134 LPC1776 LPC1756 LPC2468 LPC2377 LPC1853 LPC1112 LPC11U34/311 LPC1765 LPC1346 LPC1347 LPC2138 LPC1768 LPC4076 LPC4072 LPC2144 LPC1759 LPC1754 LPC1114/203 LPC11E11/101 LPC11U35/401 LPC11C24/301 LPC2142 LPC1769 LPC1752 LPC2210 LPC1786 LPC11D14/302 LPC2378 LPC2106 LPC1112/101 LPC11E14/401 LPC11U23/301 LPC11U37/501 LPC2109 LPC11U34/421 LPC11U24/301 LPC2104 LPC2106 LPC11U36/401 LPC1787 LPC2106 LPC11A12/101 LPC2378 LPC4088 LPC2105 LPC2148 LPC4310 LPC3180 LPC4300 LPC3131 LPC3143 LPC3154 LPC4357 LPC3141 LPC4310 LPC4300 LPC2460 LPC4353 LPC1857 LPC4350 LPC3240 LPC2468 LPC3220 LPC3180 LPC3100 LPC2101 LPC2124 LPC2102 LPC2103 LPC2104 LPC2105 LPC2106 LPC2109 LPC2114 LPC2119 LPC2124 LPC2129 LPC2131 LPC2132 LPC2134 LPC2136 LPC2138 LPC2141 LPC2142 LPC2144 LPC2146 LPC2148 LPC2157 LPC2158 LPC2194 LPC2210 LPC2212 LPC2214 LPC2220 LPC2290 LPC2292 LPC2294 LPC2361 LPC2362 LPC2364 LPC2365 LPC2366 LPC2367 LPC2368 LPC2377 LPC2378 LPC2387 LPC2388 LPC2420 LPC2458 LPC2460 LPC2468 LPC2470 LPC2478 LPC2880 LPC2888 LPC4072 LPC4074 LPC4076 LPC4078 LPC4088 LPC810 LPC811 LPC812
How to reverse engineer a microchip?
1. Software attack
We usually exploit a protocol or encryption algorithm encryption weakness to perform an decryption. The weakness in the design of the erasing operation sequence in the early ATMEL AT89C microcontrollers was exploited in a successful software attack. Once the next erasing of program data in on-chip program memory is being prevented after erasing the encryption lock bit, An unencrypted single-chip microcomputer (MCU) will occur that could be read with a programmer.
It’s possible to research and develop software attacks using other encryption algorithms. There are flaws in the development process that make it possible for some programmers to locate and insert bytes. Find whether there are constant vacancies in the chip by locating continuous FFFF bytes, which execute the chip’s program and then send it to the off-chip, and then intercept the decrypted device.
2. Electronic detection attack
This technique is used to decrypt the encrypted MCU programmes. A microcontroller’s analog connections and emissions are monitored for high temporal resolution during operation to detect an attack. Because operating instructions cause power consumption to fluctuate, observing the electromagnetic emissions allows for detection of specific information. Using statistical analysis and electronic measuring equipment, this approach is able to infer specific information from microcontroller power consumption changes.
3. Fault generation technology
Fault-based attacks are accomplished by exploiting the processor’s vulnerability to abnormal operating conditions. Voltage and clock surges are the most common fault-generating attacks. The processor can be disabled by low-voltage or high-voltage attacks, or it can be forced to perform incorrect operations. Fault-based attacks can be used to disable protection circuitry or force the processor to perform the wrong things. Even though protected data is not destroyed, a protection circuit may be reset by clock transients. In some processors, individual instructions may not be decoded and executed correctly.
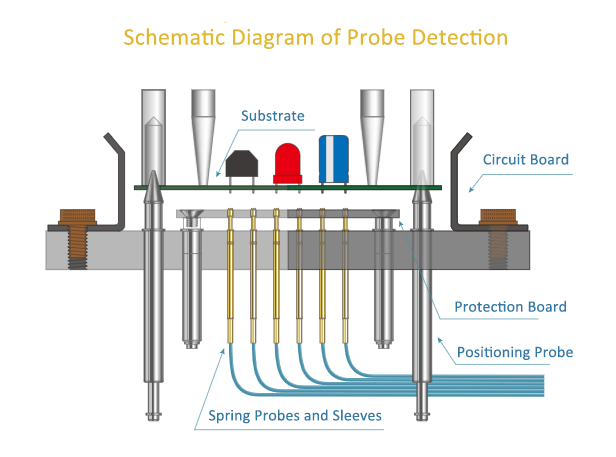
4. Probe test Decrypt
Flying Probe Test is commonly used for IC and circuit board (PCB) testing. We can assess an IC’s functionality by transmitting a current and frequency from the test object to a testing substrate using probe sockets or fixtures. Additionally, we can directly view and decrypt the internal wiring of the microcontroller.
5. UV attack method
UV attack, also known as UV irradiation method. It is used to erase the encryption on One Time Programmable (OTP) chips. An OTP chip, which has become an unencrypted chip after being UV irradiated, can be directly read using a programmer.

6. Exploiting chip vulnerabilities
Chips are frequently created with encryption flaws, allowing attackers to read the code stored in memory. For example, the code on a chip may have contact FFs, which can be used to decrypt the code. By inserting bytes, you can accomplish decryption if you can find these FFs.

You can also search for a certain byte in the code to decrypt the program. ATMEL’s 51 series AT89C51 decryption is decrypted by exploiting a byte vulnerability in the code.
7. FIB recovery encryption fuse method
FIB (Focused Ion Beam) devices are usually used to reconnect a line or restore a line with laser-altered equipment. This method is not the finest because it requires equipment and consumables. However, if there are a lot of chips that must be unlocked, this approach will be excellent. At first, the wafer in the chip is exposed by dissolving a specific lipid. Then, a high-powered microscope and FIB are used to locate the encrypted location of the chip. After the chip is exposed, its circuit is altered so that it is decrypted. Finally, the programmer is used to read the program out of the chip.


Many chips with fuse encryption can be decrypted using this method. The MSP430 is one of the most prominent examples because the MSP430 must burn the fuse when encrypting. If the fuse can be restored, it will become an unencrypted chips, such as MSP430F1101A, MSP430F149, MSP430F425, etc.
8. The method of modifying the encrypted line
CPLD and DSP chips are difficult to decrypt with the method described above, and they have high encryption performance. To decrypt these chips, you must first understand their structure, then search for the encryption circuit, and then use the chip’s circuit to modify the device. Make some alterations to the circuit of a chip so that the encryption circuit is not working, and the encrypted CPLD or DSP becomes unlocked so that the code can be accessed. TMS320LF2407A decryption, TMS320F28335 decryption, and TMS320F2812 decryption are examples of this approach.
Why Choose Us?

15 Years Experiences
Our IC development and decryption experts have over 13 years of technical experience.
Guaranteed Benefit
We promise that if your IC decryption project is unsuccessful, no related fees will be charged.
Advanded Equipment
We utilise Focused Ion Beam (FIB), Scanning Electron Microscope (SEM), and Transmission Electron Equipment (TEM) to provide the best service possible.
Explore More About IC Knowledges

How to Cut PCBs? Essential Tools, Methods and Expert Guides
PCB cutting can make or break your electronics project. Whether you’re crafting a one-of-a-kind prototype or preparing for mass production, getting it right is essential.

RP2040 – Raspberry Pi’s Microcontroller Breakdown
If you’ve been dipping your toes into the world of embedded systems or DIY electronics, you’ve likely heard whispers about the RP2040. But what exactly

AlphaEvolve-Google’s AI Agent Revolutionizing Algorithm Discovery
In the heart of AI’s next frontier stands AlphaEvolve, Google DeepMind’s groundbreaking agent that’s turning centuries-old mathematical puzzles into footnotes. This self-evolving AI doesn’t just
