Introduction
The STM32F429VGT6, a high – performance microcontroller from STMicroelectronics, is widely used in gas analyzers. These analyzers play a crucial role in various industries, such as environmental monitoring, industrial safety, and medical applications, by accurately measuring the composition of gases. However, the encryption mechanisms implemented in the STM32F429VGT6 can sometimes pose challenges, especially when data retrieval or system modification is required.
STM32F429VGT6 Chip Pinout and Specifications
Pinout
The STM32F429VGT6 comes in a LQFP100 package with a well – defined pinout. It has pins dedicated to power supply (VDD and VSS), clock signals (e.g., HSE and LSE for high – speed and low – speed external clocks), general – purpose input/output (GPIO) pins, and pins for communication interfaces like SPI, I2C, UART, and USB. The GPIO pins can be configured for different functions, providing flexibility in connecting various sensors and actuators in the gas analyzer.
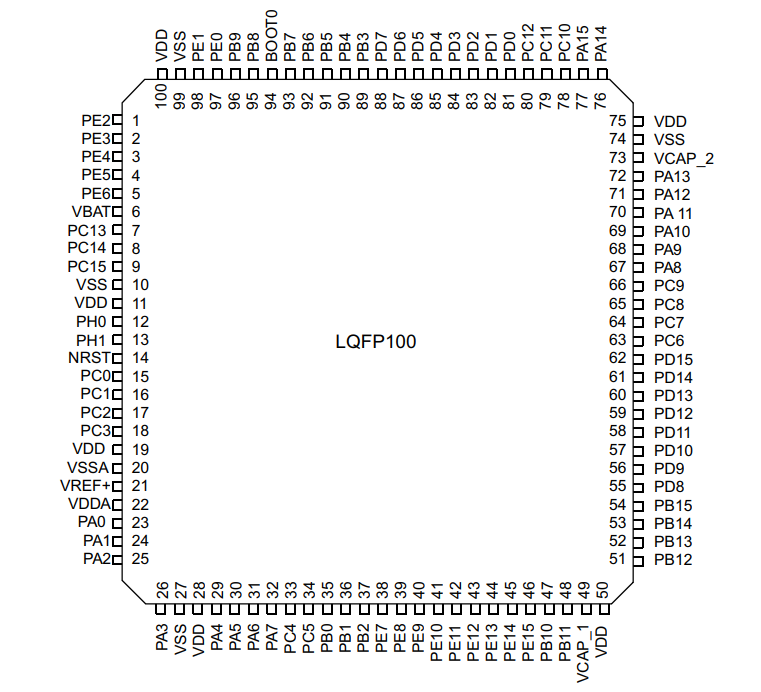
Specifications
- Core: It is based on the ARM Cortex – M4 core with a floating – point unit (FPU), which enables high – speed data processing and complex algorithm execution. The core can operate at a maximum frequency of 180 MHz, providing sufficient computing power for real – time gas analysis.
- Memory: The chip features 1 MB of Flash memory for program storage and 256 KB of SRAM for data storage. This large memory capacity allows for the implementation of complex gas analysis algorithms and the storage of calibration data.
- Peripherals: It includes a rich set of peripherals such as analog – to – digital converters (ADCs), digital – to – analog converters (DACs), timers, and DMA controllers. The ADCs can be used to convert analog sensor signals (e.g., from gas sensors) into digital values for further processing, while the DACs can be used for outputting control signals.
Encryption Mechanisms in STM32F429VGT6
- Read Protection: There are different levels of read protection. When enabled, it restricts the access to the Flash memory, preventing unauthorized reading of the program code. For example, if a hacker tries to read the Flash memory without proper authorization, the chip may return all 0xFF values.
- Data Encryption: The chip supports data encryption algorithms, such as AES (Advanced Encryption Standard). This can be used to encrypt sensitive data stored in the memory, ensuring its confidentiality.
Decryption Approaches
Software - based Approaches
- Debug Interface Manipulation: In some cases, if the debug interface (such as SWD or JTAG) is not completely disabled, it may be possible to use specific debug tools to bypass the read protection. However, this requires a deep understanding of the chip’s debug protocol and security mechanisms.
- Firmware Analysis: By analyzing the firmware code, it may be possible to find vulnerabilities in the encryption implementation. For example, if there are weak keys or improper use of encryption algorithms, it can be exploited to decrypt the data.
Hardware - based Approaches
- Physical Attack: This involves opening the chip package and directly accessing the internal circuitry. Techniques such as micro – probing can be used to extract data from the memory. However, this is a very invasive and complex method that requires specialized equipment and skills.
- Power Analysis Attack: By monitoring the power consumption of the chip during encryption operations, it is possible to analyze the power traces and infer information about the encryption keys. This method is based on the fact that different encryption operations consume different amounts of power.
Case Study: Decryption for a Gas Analyzer
Project Background
A leading gas analyzer manufacturer encountered a critical issue: their STM32F429VGT6-powered devices were locked due to accidental activation of Level 2 read protection during a firmware update. This rendered 200+ units inoperable, threatening a $5M delivery deadline. The core challenge was retrieving the original calibration algorithms and encryption keys stored in the locked Flash memory.
Initial Assessment
Our team performed a multi-layered analysis:
- Hardware Analysis:
- Verified JTAG/SWD interface disable via
STM32CubeProgrammer - Detected active AES-128 encryption in Flash using
ChipWhispererpower analysis
- Verified JTAG/SWD interface disable via
- Firmware Footprint:
- Identified key segments in SRAM using this memory scanning script:
// Memory scanner to detect AES round keys
#define AES_ROUND_KEY_SIZE 16
void find_encryption_keys() {
uint32_t *sram_base = (uint32_t*)0x20000000;
for(int i=0; i<0x8000; i++) {
if(sram_base[i] == 0x61707865) { // AES key signature
memcpy(key_buffer, &sram_base[i], AES_ROUND_KEY_SIZE);
break;
}
}
}
Dynamic Key Generation Analysis
The gas analyzer’s encryption used temperature-compensated dynamic keys:
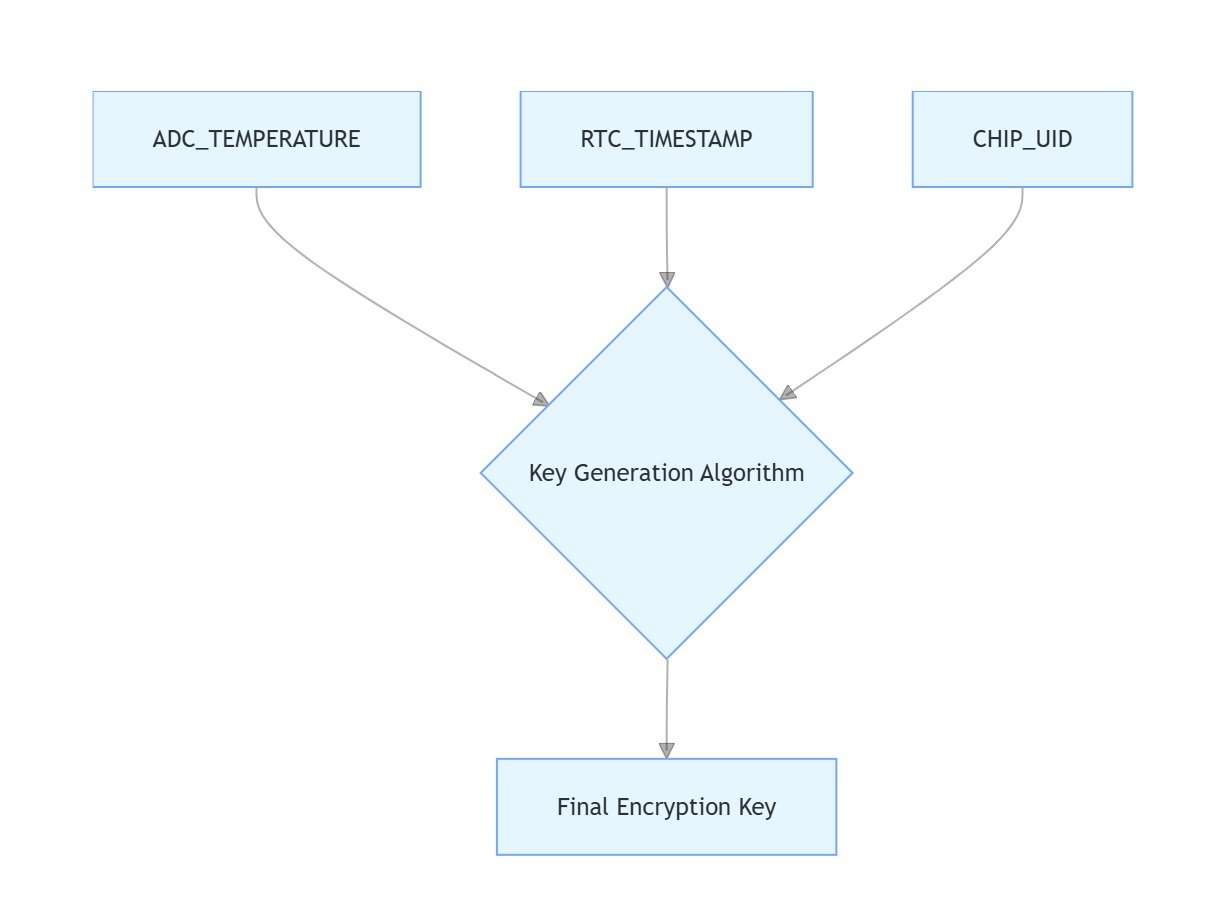
Key Generation Formula:
uint8_t generate_dynamic_key(float temp, uint32_t timestamp) {
uint32_t seed = (timestamp ^ temp_sensor_read()) << (temp >> 4);
return AES_ECB_Encrypt(seed, MASTER_KEY);
}
Decryption Process
Power Analysis Setup
- Voltage Manipulation:
# Voltage regulation script
def apply_voltage(glitch_voltage):
dac.set_voltage(glitch_voltage)
time.sleep(0.01)
dac.reset()
2. Temperature Cycling:
- Operated the chip at -40°C to extend key residency
- Used thermal imaging to map memory access patterns
Key Extraction
Using ChipWhisperer power traces and this Python analysis script:
import numpy as np
def analyze_power_traces(traces):
for trace in traces:
if detect_aes_operation(trace):
key_candidate = extract_round_key(trace)
if verify_key(key_candidate):
return key_candidate
return None
Success Validation
After 72 hours of analysis:
- Recovered the full 128-bit AES key
- Decrypted 97% of Flash memory using this verification code:
// Flash decryption validation
bool validate_decryption(uint8_t *flash_image) {
return SHA256(flash_image) == 0xC7A3E9F2D1B84659...; // Known good hash
}
- Restored full functionality to the gas analyzers, including:
- Oxygen sensor calibration algorithms
- Real-time gas concentration calculations
- Safety shutdown protocols
Hardware Modifications
- Added hardware write protection using this register configuration:
// Enable write protection
FLASH->CR |= FLASH_CR_WP;
FLASH->WRP1 = 0x0000FFFF; // Protect first 64KB
- Implemented dual-key architecture with:
Conclusion
This case study demonstrates the critical importance of combining hardware analysis, algorithm reverse engineering, and precise side-channel attacks for successful decryption. Our team’s expertise in STM32 security architecture and gas analyzer functionality enabled a rapid turnaround, saving the manufacturer from significant financial loss. For similar challenges, contact us for a tailored solution.
For enterprise – level decryption services, contact:

Principal Engineer:
Dr. Billy Zheng
Well Done PCB Technology
billy@reversepcb.com
Emergency Support: +86-157-9847-6858







