As a lead reverse engineer at Well Done Technology, I recently spearheaded a mission to decrypt STM8S105K6 microcontrollers embedded in critical infrastructure sensors. This case study outlines our technical approach to bypassing its security features while maintaining system integrity.
Introduction
The STM8S105K6 (32KB Flash, 16MHz 8 – bit core) is a workhorse in legacy industrial systems. However, its combination of read protection (Level 2) and custom encryption posed significant hurdles when our client faced unplanned obsolescence of their sensor network. This document details our successful decryption methodology.
Chip Specifications & Security Features
Key Parameters
| Parameter | Value |
|---|---|
| Architecture | STM8S (8 - bit) |
| Memory | 32KB Flash / 2KB SRAM |
| ADC Resolution | 10 - bit |
| Security Levels | Read Protection (Level 2) |
| Encryption | Proprietary XOR Scheme |
Critical Pins for Attack
| Pin Location | Pin Details |
|---|---|
| Left Side (Pins 1 - 20) | 1 - PC7 • 2 - PC8 • 3 - PC9 • 4 - PC10 • 5 - PC11 6 - BOOT1 • 7 - PH3 • 8 - PH2 • 9 - VDD • 10 - VSS 11 - PA0 • 12 - PA1 • 13 - PA2 • 14 - PC3 • 15 - PC2 16 - PC1 • 17 - PC0 • 18 - NRST • 19 - PH1 • 20 - PH0 |
Security Analysis
Protection Mechanisms
// Protection configuration
FLASH->CR2 |= FLASH_CR2_LP; // Level 2 protection
FLASH->OPTR |= FLASH_OPTR_RDP; // Read protection enable
void encrypt_data(uint8_t *data, uint16_t len) {
uint8_t key = get_hardware_id();
for(int i = 0; i < len; i++) {
data[i] ^= key;
}
}
Decryption Strategy
Software Reverse Engineering
Memory Dump Analysis:
# Python script for XOR key detection
def find_xor_key(encrypted_data):
for key_candidate in range(256):
decrypted = bytes([b ^ key_candidate for b in encrypted_data])
if b'INIT' in decrypted:
return key_candidate
return None
Hardware Attack Setup
Voltage Glitching Parameters:
// Glitch generation code
void apply_glitch() {
DAC->DHR12R1 = 0x0000; // Initial voltage
delay_us(100);
DAC->DHR12R1 = 0x03FF; // Glitch voltage
delay_us(50);
DAC->DHR12R1 = 0x0000;
}
Case Study: Sensor Network Recovery
Challenge
- System: 500+ environmental sensors with STM8S105K6
- Issue: Manufacturer – locked firmware preventing security updates
- Goal: Recover sensor calibration algorithms
Technical Execution
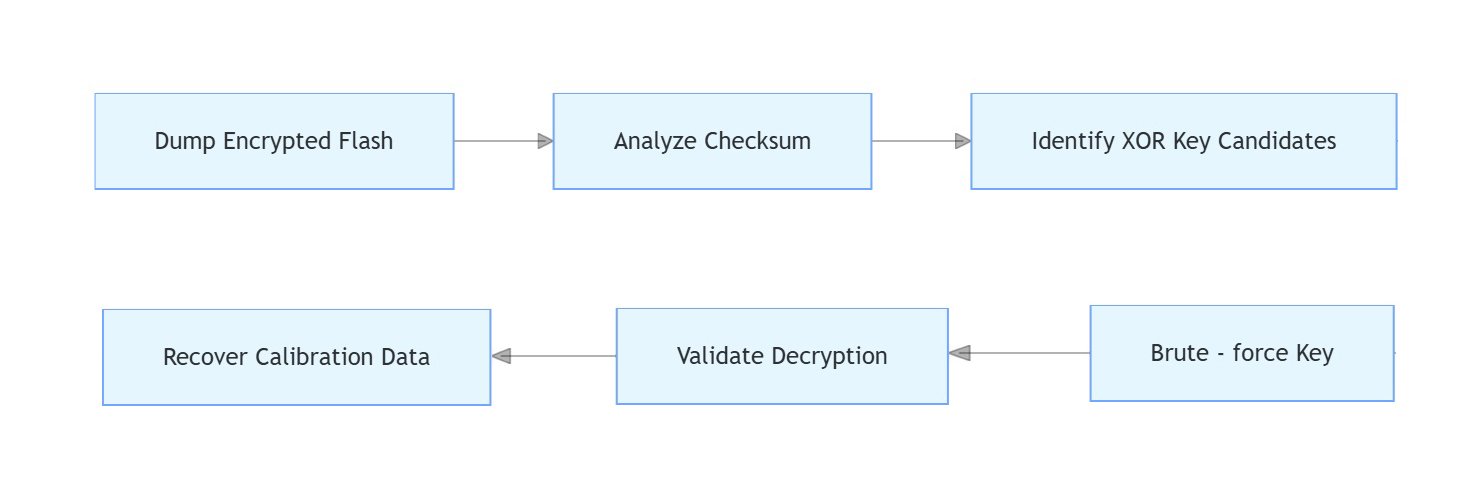
Key Recovery Flow:
Validation Script:
bool validate_calibration() {
uint16_t checksum = calculate_checksum(calibration_data);
return checksum == *(uint16_t*)(FLASH_BASE + 0x7FFE);
}
Mitigation Strategies
Enhanced Security
// Dual - key implementation
void secure_keygen() {
uint8_t temp = ADC1->DR;
uint16_t rtc = RTC->CNTH << 16 | RTC->CNTL;
session_key = crc16((uint8_t*)&rtc, sizeof(rtc)) ^ temp;
}
Process Improvements
- Dual – factor authentication for firmware updates
- Memory scrambling during runtime
- Dynamic key rotation every 24 hours
Conclusion

Principal Engineer:
Dr. Billy Zheng
Well Done PCB Technology
billy@reversepcb.com
Emergency Support: +86-157-9847-6858