What is IC Unlock?
IC unlock is aslo called IC decrypt, IC attack or IC crack. An IC (integrated circuit) is usually encrypted when it was being finished manufactured. An IC unlock service decrypts ICs through semiconductor reverse engineering. When the IC is decrypted, the programmer is able to read its programming.
8 Effective Ways for IC Unlock or Decrypt
Attackers can extract critical information from the IC or MCU and obtain the program through chip design flaws or software defects. Technical methods can be used to obtain this information. Below are common 8 ways:
1. Software attack
The technique typically uses processor communication interfaces and exploits protocols, encryption algorithms, or security holes in these algorithms to perform attacks. A typical example of a successful software attack is the attack on the early ATMEL AT89C series microcontrollers. The attacker took advantage of the loopholes in the design of the erasing operation sequence of this series of single-chip microcomputers. After erasing the encryption lock bit, the attacker stopped the next operation of erasing the data in the on-chip program memory, so that the encrypted single-chip microcomputer becomes Unencrypted single-chip microcomputer, and then use the programmer to read the on-chip program.
As for other encryption methods, some equipment can be researched, and some software can be used to do software attacks. Recently, a Kikidi Technology 51 chip decryption device (made by a master in Chengdu) has appeared in China. This decryptor is mainly aimed at SyncMos.Winbond. It has loopholes in the production process and uses some programmers to locate and insert bytes. Find whether there are continuous vacancies in the chip by a certain method, that is to say, find the continuous FFFF bytes in the chip, the inserted bytes can execute the instructions to send the program on the chip to the off-chip, and then use the decrypted device to intercept , so that the program inside the chip is decrypted.
2. Electronic detection attack
This technique typically monitors the analog characteristics of all power and interface connections of the processor during normal operation with high temporal resolution, and implements the attack by monitoring its electromagnetic radiation characteristics. Because the microcontroller is an active electronic device, when it executes different instructions, the corresponding power consumption also changes accordingly.
In this way, by analyzing and detecting these changes using special electronic measuring instruments and mathematical statistical methods, specific key information in the microcontroller can be obtained. As for the RF programmer can directly read the program in the old encrypted MCU, this principle is adopted.
3. Fault generation technology
The technique uses abnormal operating conditions to fault the processor and then provides additional access to carry out the attack. The most widely used fault-generating attacks include voltage surges and clock surges. Low-voltage and high-voltage attacks can be used to disable protection circuits or force the processor to perform erroneous operations. Clock transients may reset the protection circuit without destroying the protected information. Power and clock transients can affect the decoding and execution of individual instructions in some processors.
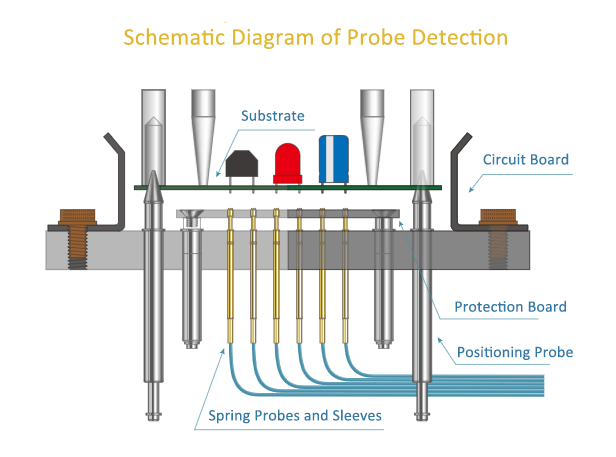
4. Probe test
The probe test technology is widely used in IC and circuit board (PCB) testing. We can determine the performance of IC unlock by transmitting a current and frequency from the testing object to a testing substrate through probe sockets or fixtures. Further more, the internal wiring of the microcontroller can directly exposed for observing and decryption.
5. UV attack method
Ultraviolet attack, also known as UV attack method, is to use ultraviolet rays to irradiate the chip, so that the encrypted chip becomes an unencrypted chip, and then use the programmer to directly read the program. This method is suitable for OTP chips. Engineers who do single-chip microcomputers know that OTP chips can only be erased with ultraviolet light. Then to erase the encryption also needs to use ultraviolet rays. At present, most of the OTP chips produced in Taiwan can be decrypted using this method. Those who are interested can try it or go to download some technical information.

The package of the OTP chip has a quartz window in half of the ceramic package. This kind of thing can be directly irradiated with ultraviolet light. If it is packaged in plastic, the chip needs to be opened first, and the wafer can be exposed before using ultraviolet light. Because the encryption of this chip is relatively poor, decryption basically does not require any cost, so the price of decryption of this chip in the market is very cheap, such as SN8P2511 decryption of SONIX, and Feiling MCU decryption. The price is very cheap.
6. Exploiting chip vulnerabilities
Many chips have encryption loopholes when they are designed. Such chips can use loopholes to attack the chip to read the code in the memory, such as the loopholes in the chip code mentioned in our previous article, if you can find the contact FF like this The code can insert bytes to achieve decryption.

Another is to search for a special byte in the code. If there is such a byte, you can use this byte to export the program. Such chip decryption takes Winbond and Xinmao’s single chips as examples, such as W78E516 decryption, N79E825 decryption, etc. ATMEL’s 51 series AT89C51 decryption is decrypted by exploiting the byte vulnerability of the code.
In addition, some chips have obvious loopholes. For example, when a certain pin is powered on after encryption, the encrypted chip will become an unencrypted chip. Since it involves a domestic single-chip manufacturer, the name is not listed.
At present, the chip decryptors that can be seen on the market are all exploiting the loopholes of the chip or the program to achieve decryption. However, the decryption that can be bought outside basically has very few models that can be solved, because generally decryption companies will not publish or transfer the core things to the outside world. For the convenience of decryption, the decryption company will use its own decryption tool.
7. FIB recovery encryption fuse method
This method is suitable for many chips with fuse encryption. The most representative chip is TI’s MSP430 decryption method, because the MSP430 needs to burn the fuse when encrypting. So, as long as the fuse can be restored, it will become an unencrypted chip, such as MSP430F1101A, MSP430F149, MSP430F425, etc. Generally, decryption companies use probes to connect the fuse bits. Some people, because they do not have too many decryption devices, need to be modified by other semiconductor circuit modification companies.

Generally, FIB (Focused Ion Beam) can be used. equipment to connect the line, or restore the line with special laser-modified equipment. There are a lot of second-hand equipment in China, and the price is very cheap. Some powerful decryption companies have equipped their own equipment. This method is not a good method because it requires equipment and consumables, but if there is no better method for many chips, this method is needed to achieve.
8. The method of modifying the encrypted line
At present, the CPLD and DSP chips on the market are complex in design and have high encryption performance. It is difficult to decrypt using the above method. Therefore, it is necessary to analyze the chip structure, and then find the encryption circuit, and then use the chip circuit to modify the equipment. Make some modifications to the circuit of the chip, make the encryption circuit invalid, and make the encrypted DSP or CPLD become an unencrypted chip so that the code can be read. Such as TMS320LF2407A decryption, TMS320F28335 decryption, TMS320F2812 decryption is to use this method.
IC Unlock Service
We provide professional IC unlock services. The program code is extracted from embedded chips such as DSP, ARM, and MCU, and the circuit diagram and PCB file are extracted by mapping the PCB circuit board. After obtaining the chip program and PCB circuit diagram, analysis and research can be carried out for secondary development.
For enterprise – level decryption services, please contact:

Principal Engineer:
Dr. Billy Zheng
Well Done PCB Technology
billy@reversepcb.com
Emergency Support: +86-157-9847-6858






